Feb, 21, 2023, /DCD/ - A security firm has found evidence of an ongoing campaign to steal customer data from a number of data center firms.
First reported by Bloomberg, endpoint security firm Resecurity has found evidence of at least two data center firms being compromised, with further attempts on several others.
The compromised data caches reportedly involve emails and passwords for customer-support websites for GDS Holdings and ST Telemedia Global Data Centres (STT GDC), according to the publication. Both companies said the compromised information posed no risk to clients’ IT systems or data.
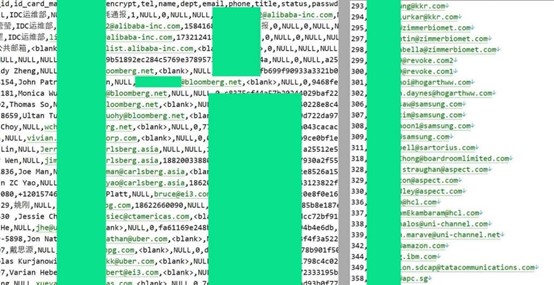
Bloomberg notes customers affected include Alibaba, Amazon, Huawei, Baidu, Apple, Goldman Sachs, BMW, Bank of America, Bank of China, Bharti Airtel, ByteDance, Ford, Globe Telecom, Mastercard, Morgan Stanley, Paypal, Porsche, SoftBank, Telstra, Tencent, Verizon, Wells Fargo, Walmart, and Bloomberg’s own parent company.
Around 2,000 customers of GDS and STT GDC were reportedly affected, with at least five accounts actually logged into – including China’s main foreign exchange and debt trading platform and four others from India.
“The application which was targeted by hackers is limited in scope and information to non-critical service functions, such as making ticketing requests, scheduling physical delivery of equipment and reviewing maintenance reports,” according to a GDS statement to the publication. “Requests made through the application typically require offline follow up and confirmation. Given the basic nature of the application, the breach did not result in any threat to our customers’ IT operations.”
On more recent attacks, GDS said: “Recently, we detected multiple new attacks from hackers using the old account access information. We have used various technical tools to block these attacks. So far, we haven’t found any new successful break-in from hackers which is due to our system vulnerability.”
“As we are aware, one single customer didn’t reset one of their account passwords to this application which belonged to an ex-employee of theirs. That is the reason why we recently forced a password reset for all the users. We believe this is an isolated event. It is not a result of hackers breaking through our security system.”
STT GDC said it brought in external cybersecurity experts when it learned about the incident in 2021. “The IT system in question is a customer service ticketing tool” and “has no connection to other corporate systems nor any critical data infrastructure,” the company said.
The company said its customer service portal wasn’t breached in 2021 and that the credentials obtained by Resecurity are “a partial and outdated list of user credentials for our customer ticketing applications. Any such data is now invalid and does not pose a security risk going forward.”
“No unauthorized access or data loss was observed,” according to STT GDC’s statement.
30,000 data center CCTV cameras compromised
In its own blog, Resecurity said it notified several data center organizations about malicious cyber activity targeting them and their customers, with initial early warnings sent around September 2021 with further updates during 2022 and January, 2023.
“Some contacts confirming the use of the credentials have been utilized by them and their IT staff, and that data center was used either for disaster recovery or active operations in the APAC region,” the company said. “Notably, some of the interviewed organizations stated how they never received any notification about any possible incidents resulting in their credential leakage and were not aware of it. Some organizations confirmed the opposite, and they received certain communications about the need to change passwords.”
The company said credentials to ‘presumably related data center organizations’ have been recently published to Breached.to, an underground forum, and had seen some of the stolen data for sale on another dark web community known as RAMP/RAMP4U.
ReSecurity said most customer organizations identified in the leaked data sets relate to financial institutions with a global presence, investment funds, biomedical research companies, technology vendors, eCommerce, online marketplaces, cloud services, ISPs, and CDN providers with operations in the US, UK, Canada, Australia, Switzerland, New Zealand, and China.
Resecurity noted the activity has been shared with the affected parties and national computer emergency response teams (CERTs) in China and Singapore, as well as US Law enforcement, for further analysis and risk mitigation.
The security firm said that in one of the cases, threat actors likely gained initial access via a vulnerable helpdesk or ticket management module integrated with other applications and systems, allowing the attack to pivot and move to other systems.
The threat actor was reportedly able to extract a list of some 30,000 CCTV cameras used to monitor data center environments, as well as credential information for IT staff at the data center. Many of the cameras reportedly had simple passwords such as “admin” or “admin12345.” The attacker then sought to collect information about the representatives managing operations on behalf of enterprises, lists of purchased services, and deployed equipment, as well as monitor video streams of clients' equipment deployed in the data center.
“Unfortunately, we haven't received any feedback in this regard from the affected parties,” the company said.
The campaign also saw the data – possibly credentials, e-mail, cellphone, and ID card references – of around 2,000 companies collected from one company.
“After communication with CNCERT/CC around January 24, 2023, the affected organization forced customers to change their passwords,” Resecurity said.
The threat actor also compromised one of the internal email accounts used to register visitors, which can provide key information about the exact staff responsible for data center operations from the client side.
A second Singapore-based company saw a customer database containing around 1,210 records exfiltrated.
“Based on our assessment, the activity was successfully detected by the affected party,” said Resecurity.
The security firm said it found evidence of further access attempts to customer portals of 10 different organizations, some of which were based in India.
Another part of the campaign reportedly involves a US-based organization operating in a carrier-neutral data center and was a client of one of the previously impacted data centers abroad.
“Resecurity was able to collect several credentials used by the IT staff which granted access to the customer portal in another data center, and also several screenshots of their client’s successful authorizations,” said Resecurity.
Which group is behind the attack is unclear. At this stage, Resecurity said it hasn't identified any notable hits with known APT groups.
In a statement, Microsoft told Bloomberg: “We regularly monitor for threats that could impact Microsoft and when potential threats are identified we take appropriate action to protect Microsoft and our customers.”
A spokesperson for Goldman Sachs said, “We have in place additional controls to protect against this type of breach and we are satisfied that our data was not at risk.”
Automaker BMW said it was aware of the issue and told Bloomberg: “After assessment, the issue has a very limited impact on BMW businesses and has caused no damage to BMW customers and product-related information. BMW has urged GDS to improve the information security level.”
Cheryl Lee, a spokesperson for the Cyber Security Agency of Singapore, said the agency “is aware of the incident and is assisting ST Telemedia on this matter.”
In a statement, Baidu said: “We do not believe that any data was compromised. Baidu pays great attention to ensure the data security of our customers. We will keep a close eye on matters such as this and remain on alert to any emerging threats to data security in any part of our operations.”
A representative for Porsche said: “In this specific case we have no indication that there was any risk.”
A SoftBank representative said a Chinese subsidiary stopped using GDS last year: “No customer information data leakage from the local China company has been confirmed, nor has there been any impact on its business and services.”
A spokesperson for Telstra said: “We are not aware of any impact to the business following this breach.”
A Mastercard representative said: “While we continue to monitor this situation, we are not aware of any risks to our business or impact to our transaction network or systems.”
A representative for Tencent said: “We are not aware of any impact to the business following this breach. We manage our servers inside data centers directly, with data center facility operators having no access to any data stored on Tencent servers. We have not discovered any unauthorized access of our IT systems and servers after investigation, which remain safe and secure.”
A spokesperson for Wells Fargo said it used GDS for backup IT infrastructure until December 2022: “GDS did not have access to Wells Fargo data, systems, or the Wells Fargo network."